In our previous blog, we mentioned 3 strategies of Penetration Testing which define main approaches towards target security assessment. Now, let’s dive deeper and see into which of them is more suitable in certain situations. The main factors that we’ll use here are cost of assessment vs assessment coverage.
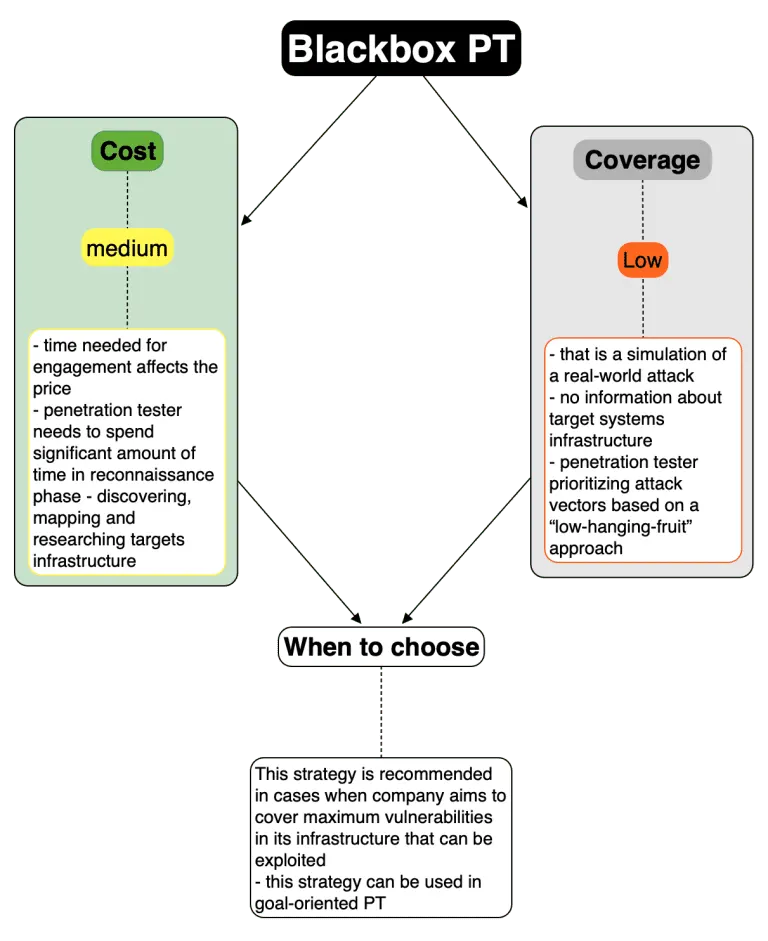
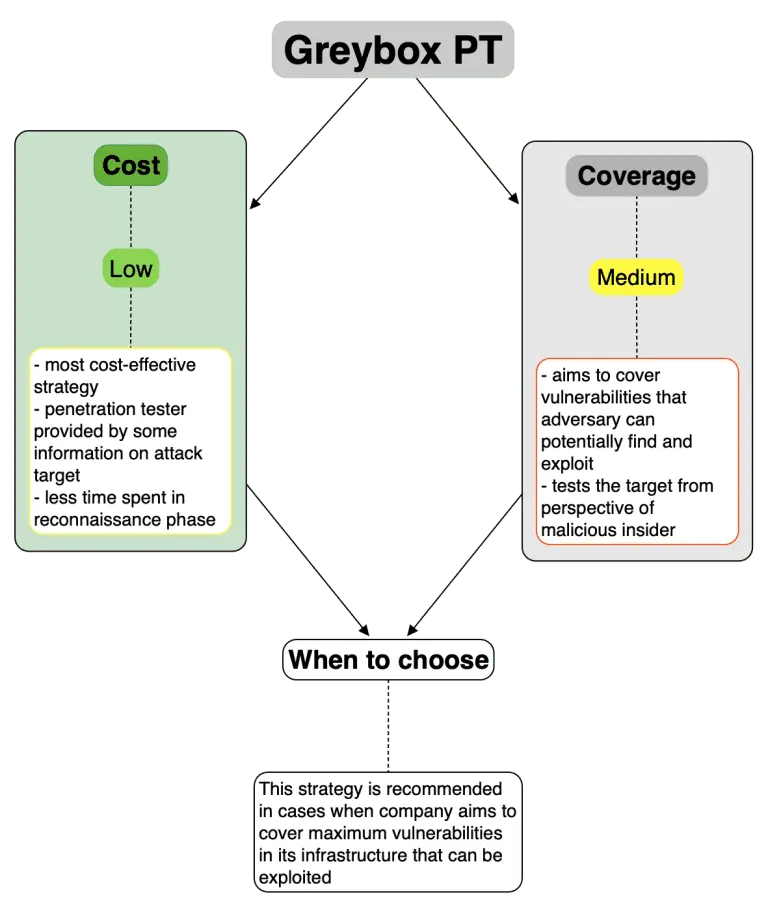
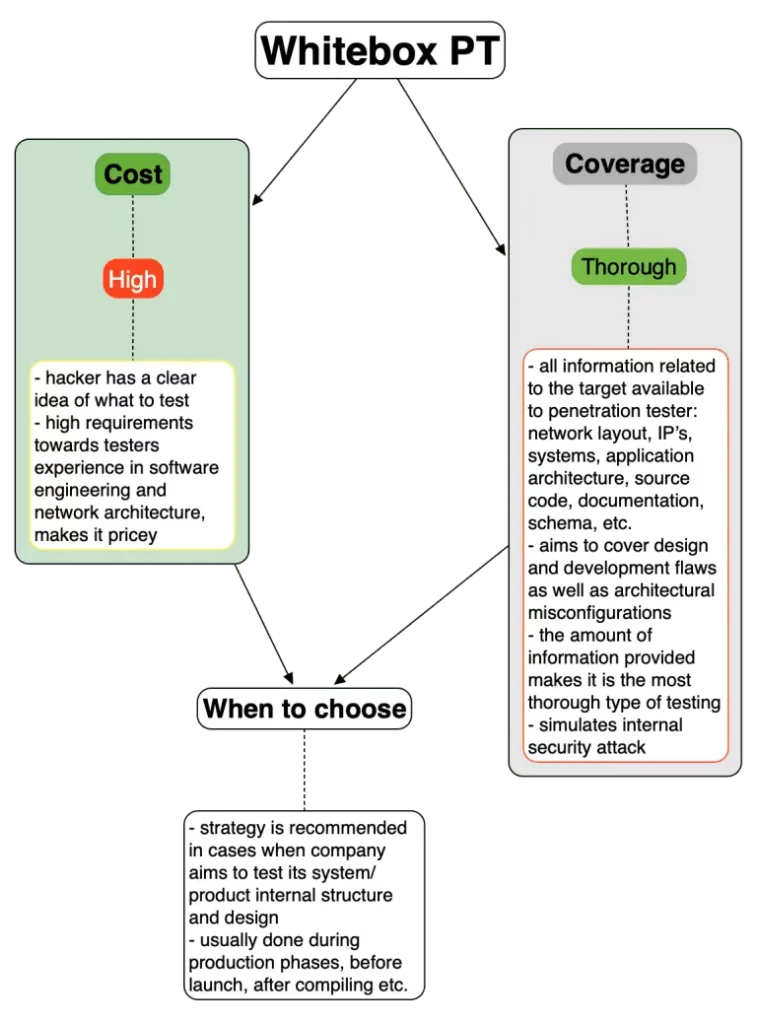
As a final word, it should be stated that there are now strict boundaries on which testing strategy to use (except common sense ofcourse). As well as there are no strict borders and limitations between use of those three. In the wild you may often see greybox engagement that has attributes of whitebox, or engagement started out as blackbox migrated to greybox under certain circumstances.
Mykhailo Kuzubov – Cybersecurity Specialist
Join us Behind the Shield
Your Monthly Pass to Cybersecurity Insights.



